Step 5: Recommend controls
Recommended Controls are specific measures, policies, or practices proposed to mitigate identified risks and align an organisation's security posture with its risk management objectives.
These controls aim to reduce the current risk to an acceptable level, aligning with the organisation’s target risk.
In CSFaaS, there are two ways to recommend controls:
-
Link an Existing Policy or Control to be Implemented
-
Propose Additional Recommended Controls (text box).
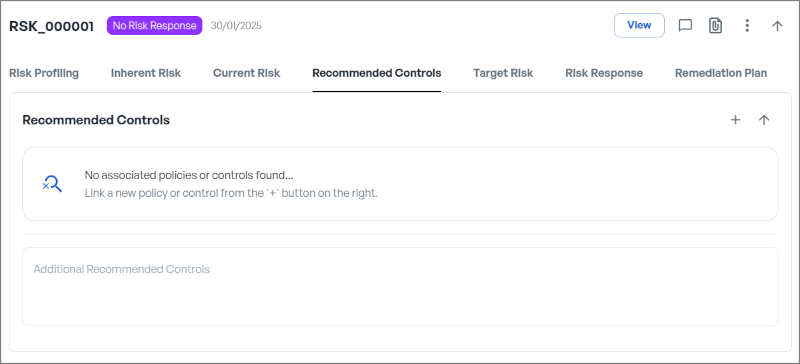
1. Link an existing policy or a control to be implemented
Sometimes, mitigating a security issue can be achieved by leveraging existing controls within the organisation. Often, this involves combining several policies, categories, or controls to address the risk effectively.
- In CSFaaS, you can select relevant Policies, Categories, Subcategories, and Controls to enforce and reduce risk.
- To do this, simply click the “+” button and select the appropriate Policies, Categories, Subcategories, and Controls.
- These details will then appear in your Recommended Control Card for reference and follow-up.
This approach helps ensure clarity and consistency when using existing resources for risk mitigation.
2. Propose Additional Recommended Controls.
When existing controls are insufficient to reduce risk to an acceptable level, it becomes necessary to propose specific mitigation measures in collaboration with key stakeholders.
Use the text box provided to describe these additional controls clearly and precisely.
Tips:
- Be clear and concise when proposing additional controls.
- Ensure the description is structured and actionable, making it easier to split into separate remediation plans if necessary.
- Frame your recommendations in a way that they can be integrated into existing security policies or standards for long-term improvement.
By effectively recommending controls, either by leveraging existing measures or proposing new ones, CSFaaS enables your organisation to address risks proactively, efficiently, and in alignment with its broader security objectives.