Step 3: Assess the Inherent Risk
Inherent risk refers to the level of risk that exists in the absence of any mitigating controls or measures. It represents the natural level of risk that arises from the characteristics of a specific activity, process, or system before considering any efforts to reduce or manage the risk.
Inherent Risk Statement
An Inherent Risk Statement provides a concise summary of the risk scenario in its natural state, without considering any existing or planned controls. It describes the likelihood and impact of a risk materialising if no mitigation measures are applied. The purpose is to clearly define and articulate the risk in its raw form and to set the baseline for risk analysis and comparison after implementing controls. Example: "The financial system is vulnerable to cyberattacks due to outdated security protocols, potentially leading to data breaches and financial losses."
Inherent Risk Weakness
Inherent Risk Weakness refers to the vulnerabilities, gaps, or deficiencies that contribute to the risk existing in its inherent state. It focuses on the weak points in processes, systems, or human factors that make the risk more likely or impactful. The purpose is to pinpoint specific flaws or limitations that allow the inherent risk to exist or escalate and to guide the identification of appropriate controls or remediation measures. Example: "The absence of multi-factor authentication (MFA) on user accounts increases the susceptibility to unauthorised access."
Inherent Risk Opportunity
An Inherent Risk Opportunity identifies potential benefits or positive outcomes that could arise from effectively addressing the risk. It focuses on how managing the risk might create value, enhance capabilities, or improve resilience, turning the risk into a strategic advantage. Example: "Implementing an advanced cybersecurity framework could enhance the company’s reputation and attract security-conscious clients."
Inherent Risk Summary Table
| Term | Focus | Purpose | Example |
|---|---|---|---|
| Inherent Risk Statement | Description of the risk scenario | Understand the risk's raw state | Financial system vulnerable to attacks. |
| Inherent Risk Weakness | Vulnerabilities causing the risk | Identify gaps and flaws | Lack of multi-factor authentication. |
| Inherent Risk Opportunity | Positive outcomes from addressing risk | Turn risks into strategic advantages | Improved reputation with better security. |
Impact type
Understanding the impact type is essential for assessing how a risk could affect various areas of your organisation. Risks can manifest across multiple dimensions, including financial loss, operational disruption, legal implications, reputational damage, or data breaches.
By defining and selecting the impact type, you can:
- Clarify the potential consequences of a risk materialising.
- Prioritise risk responses based on the most critical impact areas.
- Develop targeted mitigation strategies tailored to specific impact dimensions.
- Facilitate stakeholder communication by providing a clear picture of potential outcomes.
You can now select the relevant impact type from your predefined catalogues to ensure a structured and consistent approach to assessing and managing risks. This selection will also help in aligning risk responses with your organisation's strategic objectives and risk appetite.
By categorising risks based on their impact, you enable more focused decision-making and ensure that resources are allocated effectively to address the most significant threats.
Risk matrix
After defining the Impact Type, it’s time to determine your Inherent Risk Level using the Risk Matrix. This step involves evaluating the Likelihood and Impact to quantify the risk accurately.
1. Likelihood Level
Begin by defining the Likelihood of the risk materialising.
-
As a reminder:
Likelihood = Threat Level × VulnerabilityThis calculation combines the threat's severity with the system's susceptibility, providing a measurable likelihood score.
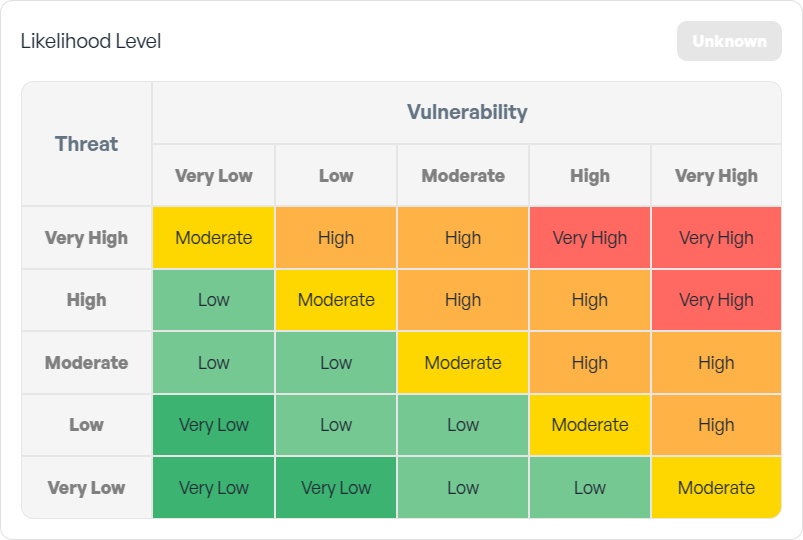
Once the Likelihood Level is defined, proceed to the Risk Exposure Matrix.
2. Risk exposure
-
As a reminder:
Risk = Likelihood x Impact.So, select the impact. Risk level will be defined automatically on the matrix.
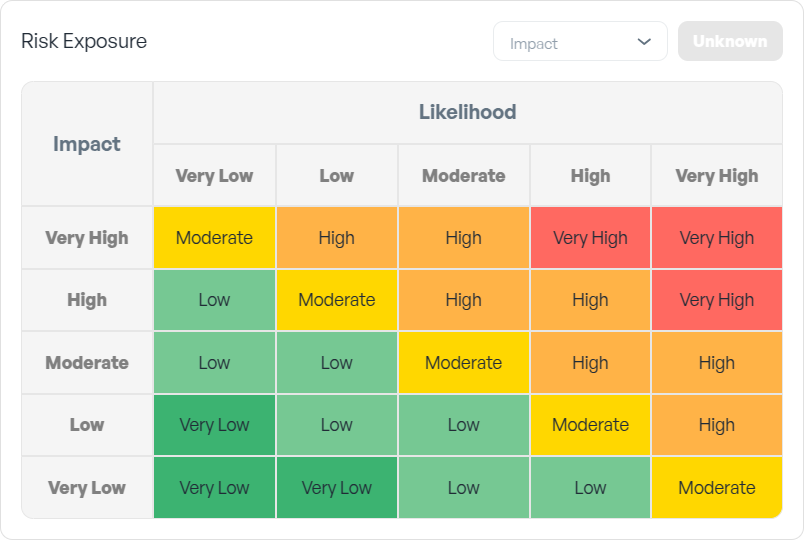
📌 Note: Likelihood Level and Risk Exposure matrix model and process taken from NIST 800-161r1, “section D.4.1.7. Risk Response Analysis” page 227 (extended from 4 levels to 5 levels).