1. Managing Risks
The Risk Registry Module, accessible from the main menu, offers a structured approach to documenting, tracking, and managing all identified cybersecurity risks. This ensures transparency, accountability, and alignment with your organization's risk appetite, strategic objectives, and business goals.
Overview
Within this module, you can:
- Monitor and Review Risks: Oversee all risks registered during the Risk Assessment Demand process, ensuring each is properly tracked and addressed.
- Mark Risks as Closed: Indicate when a risk has been mitigated or is no longer applicable.
- Delete a Risk: Remove risks that are no longer relevant.
- Define Resource Owners: Assign responsibility for each risk to specific individuals or teams.
Edit your risks
📌 Note: Risks informations in the Risk Registry Module are view-only and cannot be edited. To modify risk details, navigate to the corresponding Risk Demand entry.
Setting Risks as Closed
After setting the Risk Response and RP information, it's essential to mark each identified risk as Closed. Since a demand may contain multiple risks, each must be addressed individually.
To mark a risk as "Closed":
-
Navigate to the specific risk.
-
Click on the vertical dots in the card.

-
Click on “Mark as Closed”
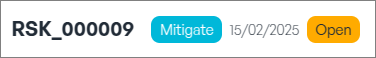
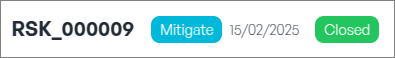
Upon completion, the status will update from "Open" to “Closed”, indicating that the risk has been officially closed in the system.
Reopening a Risk
In principle, once a risk has been closed, it should remain closed to ensure the integrity of the risk management process. Risks should not be reopened for reassessment, as each Risk Demand represents a completed evaluation cycle. If new concerns arise, a new Risk Demand should be created rather than modifying past records.
However, in some cases, reopening a risk may be necessary to update specific administrative details, such as:
- Changing the Resource Owner to reflect responsibility shifts within the organisation.
- Updating non-impacting details (e.g., metadata, classification adjustments).
How to Reopen a Risk
If reopening a risk is justified, follow these steps:
-
Navigate to the Risk Registry Module.
-
Locate the Closed risk that requires updates.
-
Click on the vertical dots in the card.

-
Select "Reopen RSK".

The risk will move back to an Open state, allowing necessary updates.


📌 Important: We strongly advise against reopening risks to modify their assessment or risk response. Once a Risk Demand has been completed, it should remain unchanged to maintain traceability and compliance with risk governance best practices.
If the risk needs reassessment due to changes in the environment or security posture, a new Risk Demand should be created instead of reopening an existing one.