6. Risk Appetite & Risk Tolerance
Weighing Risk in Decisions
Decisions to proceed must be weighed against the risk appetite and risk tolerance across the tiers of the enterprise, as well as the mitigation strategy that may be put in place to manage the risks as a result of procuring the product, service, or supplier.
Risk Appetite
Risk appetite is the amount and type of risk an organisation is willing to accept in pursuit of its objectives. It sets the overall tone for risk management and guides decision-making at all levels. Defining your risk appetite involves understanding your strategic goals, stakeholder expectations, and the capacity to manage risks.
Risk Tolerance
After establishing the risk appetite, you'll define risk tolerance, which is the acceptable level of variation relative to achieving specific objectives.
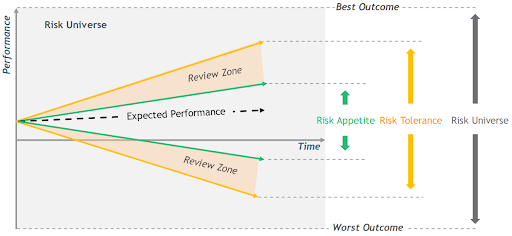
(Source NIST SP 800-161r1-upd1 Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations, p. 282.)
Distinguishing Risk Appetite and Risk Tolerance
Risk appetite statements define the overarching risk guidance, and risk tolerance statements define the specific application of that direction. This means that risk tolerance statements are always more specific than the corresponding risk appetite statements. Together, risk appetite and risk tolerance statements represent risk limits, help communicate risk expectations, and improve the focus of risk management efforts.
The definition of these risk parameters places the enterprise in a better position to identify, prioritize, treat, and monitor risks that may lead to unacceptable loss. Risk tolerance should always stay within the boundaries established by senior leadership and within the parameters of and informed by legal and regulatory requirements.
Example
| Example Enterprise Type | Example Risk Appetite Statement | Example Risk Tolerance Statement |
|---|---|---|
| Global Retail Firm | Our customers associate reliability with our company's performance, so service disruptions must be minimized for any customer-facing websites. | Regional managers may permit website outages lasting up to four hours for no more than 5% of their customers. |
| Government Agency | Mission-critical systems must be protected from known ICT vulnerabilities. | Critical software vulnerabilities (severity score of 10) must be patched on systems designated as mission-critical within 14 days of discovery. |
| Internet Service Provider | The company has a low risk appetite with regard to the failure to meet customer service-level agreements, including network availability and communication speeds. | Patches must be applied to avoid attack-related outages but must also be well-tested and deployed in a manner that does not reduce availability below agreed-upon service levels. |
| Academic Institution | The institution understands that mobile computers are a necessary part of the daily life of students, and some loss is expected. The leadership, however, has no appetite for the loss of any sensitive data (as defined by the Data Classification Policy). | Because the cost of loss prevention for students' laptops is likely to exceed the cost of the devices, it is acceptable for up to 10% to be misplaced or stolen if and only if sensitive institution information is prohibited from being stored on students' devices. |
| Healthcare Provider | The Board of Directors has decided that the enterprise has a low risk appetite for any exposures caused by inadequate access control or authentication processes. | There will always be some devices that do not yet support advanced authentication, but 100% of critical healthcare business applications must use multi-factor authentication. |
(Source NIST SP 800-221, Enterprise Impact of Information and Communications Technology Risk. Governing and Managing ICT Risk Programs Within an Enterprise Risk Portfolio, p. 20-21.)